
Support
Stroz Friedberg has responded to several incidents over the last two years that involved encryption of data at the hypervisor or datastore level. Our team has identified common tactics and techniques that threat actors have used to disrupt services on ESXi servers. Some of these TTPs include:
Detecting this malicious activity can be time consuming and challenging, especially when dealing with a significant number of logs from multiple ESXi servers or partial encryption of the logs during ransomware incidents.
To better overcome these analysis challenges, Stroz Friedberg has developed an open-source CLI tool named Quick ESXi Log Parser (“QELP”) that has enhanced investigations by swiftly parsing ESXi logs at scale and producing CSV reports in timeline format, consisting of events such as:
VMware ESXi servers are type-1 or bare-metal hypervisors1 used for creating and managing virtual resources, making them high-value assets in a network. Ransomware threat actors have identified the value in compromising ESXi servers and have transitioned from encrypting data at the endpoint and virtual machine level to encrypting data at the hypervisor level. In addition, a recent increase in ESXi vulnerabilities2 coupled with relatively few security controls at the hypervisor level enables data tampering on a larger scale and with lower effort.
Stroz Friedberg has identified common tactics and techniques utilized by threat actors to continue encrypting data at the hypervisor level. Some of the common methods include but are not limited to:
1. Enabling SSH Access: Once threat actors gain access to a network, they may enable SSH access on ESXi hosts using vCenter or Vsphere web clients, to remotely access ESXi hosts.
2. Changing Root Passwords: Threat actors may extract and edit host-profiles from the vCenter web client, edit user settings in the vSphere web client, or utilize the ESXi shell to change root passwords of ESXi servers. Changing these passwords limits access only to threat actors and hinders containment and recovery during incident response.
3. Hypervisor Encryption: Threat actors often retrieve ESXi-compatible ransomware binaries from remote servers or from local compromised systems using SSH. Final steps include deployment of the binary to encrypt data at hypervisor level, including any datastores that contain virtual machines.
Threat actor activities like those listed above can be investigated by analyzing ESXi logs. ESXi logs are stored at one of the following locations:3
1. /var/log/
2. /var/run/log/4
3. /scratch/log/
4. /tmp (if persistent logging is not enabled)
While ESXi logs can be collected manually from these locations, an easier approach is generating an ESXi support bundle. ESXi has built-in functionality to create and bundle support files for troubleshooting ESXi issues, which includes logs that are valuable for forensic analysis. An ESXi support bundle can be generated by executing the command vm-support from the ESXi shell or by following this guide.
The following logs contain information about common activities conducted by threat actors on ESXI servers.5
| Log | Forensic Value | Default Log Retention |
|---|---|---|
|
Hostd.log |
Includes details about the ESXi host agent, including:
|
Log files before rotation: 10. Maximum log size: 10 MB. |
|
Syslog.log |
Contains general logging including:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
|
Auth.log |
Consists of authentication information including:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
|
Vobd.log |
Holds details about VMkernal Observations (VOBs) including:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
|
Rhttpproxy.log |
Comprises details regarding the ESXi HTTP Reverse Proxy service, including:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
|
Shell.log |
Contains commands executed in the ESXi Shell, such as:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
|
Vmkernel.log |
Includes details about ESXi kernel, including:
|
Log files before rotation: 8. Maximum log size: 10 MB. |
|
Vmauthd.log |
Consists of details about ESXi authorization events, including:
|
Log files before rotation: 8. Maximum log size: 1 MB. |
When analyzing ESXi servers, rapid identification of the source system(s) used to access ESXi servers and of the activities conducted by threat actors in ESXi is crucial. However, this can be time consuming when handling many logs from multiple ESXi servers. Additionally, ESXi logs are often partially encrypted by threat actors, resulting in data loss, but still might contain unencrypted information relevant to the incident. Manually identifying the ESXi logs containing the most relevant information and creating a timeline of events can cost valuable analysis time. To overcome these challenges, Stroz Friedberg has developed an open-source Python script, called QELP, to automate ESXi log processing and timelining. The capabilities of QELP include:
QELP requires input directory containing ESXi support or log archives having only zip, tar, gz, or tgz extensions and an output directory for storing results.
To run QELP, execute:
rye run qelp <esxi_input_dir> <esxi_output_dir>QELP outputs CVSs containing results from respective ESXi logs as well as a timeline CSV consisting of events that are important from an incident response perspective. Following is a sample timeline generated by QELP:
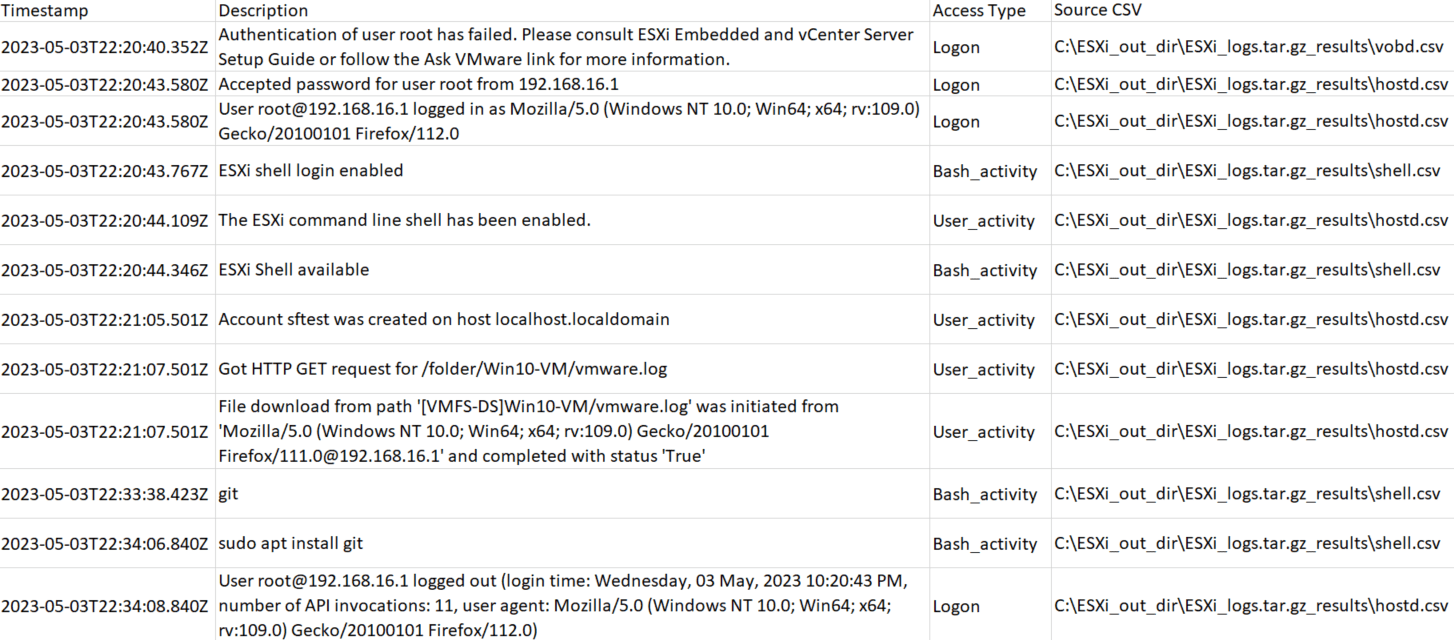
Figure 1: Sample timeline generated by QELP.
1. https://www.vmware.com/topics/bare-metal-hypervisor
2. According to CVEDetails and MITRE CVE data, in 2024, 8 VMware ESXi vulnerabilities were disclosed as compared to 2 in 2023.
3. Locations can be changed by the system administrator.
4. Can be a symbolic link for the /scratch/log/ directory.
6. During Stroz Friedberg’s testing, not every file/directory accessed via vSphere web client was captured in Syslog.log.

Support
About Cyber Solutions:
Cyber security services are offered by Stroz Friedberg Inc., its subsidiaries and affiliates. Stroz Friedberg is part of Aon’s Cyber Solutions which offers holistic cyber risk management, unsurpassed investigative skills, and proprietary technologies to help clients uncover and quantify cyber risks, protect critical assets, and recover from cyber incidents.
General Disclaimer
While care has been taken in the preparation of this material and some of the information contained within it has been obtained from sources that Stroz Friedberg believes to be reliable (including third-party sources), Stroz Friedberg does not warrant, represent, or guarantee the accuracy, adequacy, completeness or fitness for any purpose of the article and accepts no liability for any loss incurred in any way whatsoever by any person or organization who may rely upon it. It is for informational purposes only. You should consult with your own professional advisors or IT specialists before implementing any recommendation or following the guidance provided herein. Further, we endeavor to provide accurate and timely information, there can be no guarantee that such information is accurate as of the date it is received or that it will continue to be accurate in the future. Further, this article has been compiled using information available to us up to 02/10/24.
Terms of Use
The contents herein may not be reproduced, reused, reprinted or redistributed without the expressed written consent of Aon, unless otherwise authorized by Aon. To use information contained herein, please write to our team.
Stay in the loop on today's most pressing cyber security matters.
View All
Cyber Labs 17 mins
Maximizing value: How companies and pentesters can achieve more together
Cyber Labs 7 mins
DNSForge – Relaying with Force
Cyber Labs 14 mins
We’re All in This Together: The Case for Purple Teaming
Cyber Labs 7 mins
Parsing ESXi Logs for Incident Response with QELP
Cyber Labs 5 mins
Parsing Jenkins Configuration Files for Forensics and Fun
Cyber Labs 10 mins
Emerging Risks in Third-Party AI Solutions and How to Help Address Them
Cyber Labs 20 mins
Unveiling the Dark Side: Common Attacks and Vulnerabilities in Industrial Control Systems
Cyber Labs 9 mins
Mounted Guest EDR Bypass
Cyber Labs 6 mins
Optimizing Your Cyber Resilience Strategy Through CISO and CRO Connectivity
Cyber Labs 9 mins
Bypassing EDR through Retrosigned Drivers and System Time Manipulation
Cyber Labs 10 mins
DNSForge – Responding with Force
Cyber Labs 7 mins
Unveiling "sedexp": A Stealthy Linux Malware Exploiting udev Rules
Cyber Labs 3 mins
Command Injection and Path Traversal in StoneFly Storage Concentrator
Cyber Labs 7 mins
Adopt an AI Approach with Confidence, for CISOs and CIOs
Cyber Labs 3 mins
Responding to the CrowdStrike Outage: Implications for Cyber and Technology Professionals
Cyber Labs 10 mins
DUALITY Part II - Initial Access and Tradecraft Improvements
Cyber Labs 17 mins
Cracking Into Password Requirements
Cyber Labs 57 mins
DUALITY: Advanced Red Team Persistence through Self-Reinfecting DLL Backdoors for Unyielding Control
Cyber Labs 7 mins
Restricted Admin Mode – Circumventing MFA On RDP Logons
Cyber Labs 9 mins
Detecting “Effluence”, An Unauthenticated Confluence Web Shell
Ready to Explore Further?
Sign up to receive updates on the latest events, insights, news and more from our team.
Our Better Being podcast series, hosted by Aon Chief Wellbeing Officer Rachel Fellowes, explores wellbeing strategies and resilience. This season we cover human sustainability, kindness in the workplace, how to measure wellbeing, managing grief and more.

Podcast 23 mins
Better Being Series: Understanding Burnout in the Workplace
Podcast 14 mins
Better Being Series: Why Nutrition Matters
Podcast 10 mins
Better Being Series: Discover the ‘Blue Zones’ Where People Live Longer
Podcast 20 mins
Better Being Series: Improving Your Financial Wellbeing
Podcast 17 mins
Better Being Series: Are You Taking Care of Your Digital Wellbeing?
Podcast 19 mins
On Aon Podcast: Better Being Series Dives into Women’s Health
Podcast 29 mins
On Aon’s Better Being Series: The World Wellbeing Movement
Podcast 28 mins
On Aon’s Better Being Series: Mental Health and Creating Kinder Cultures
Podcast 25 mins
On Aon’s Better Being Series: Managing Loss and Grief
Podcast 24 mins
On Aon’s Better Being Series: Measuring Wellbeing
Podcast 25 mins
On Aon’s Better Being Series: Physical Wellbeing and Resilience
Podcast 24 mins
On Aon’s Better Being Series: Human SustainabilityExpert Views on Today's Risk Capital and Human Capital Issues

Article 8 mins
Thriving in an Interconnected World: How the C-Suite Embraces Uncertainty
Article 6 mins
Powering Progress: Collaborating to Build a Sustainable Future in Emerging Markets
Article 5 mins
Building Business Resilience: Key Steps to Effectively Integrate Risk Management Across Your Organisation
Article 7 mins
Why Humans Are the Essential Factor in the Success of Artificial Intelligence (AI)
Article 5 mins
Leveraging Research and Expertise to Strengthen Your HR Strategy for 2025 and Beyond
Article 5 mins
Managing Risk on the Energy Transition Journey
Article 7 mins
The Role of Risk Management in the Age of Generative Artificial Intelligence
Article 7 mins
Finding A Way In Asia Pacific's New Economic Reality
Article 4 mins
Three Ways to Boost Value from Benefits: APAC Insights from LinkedInExpert Views on Today's Risk Capital and Human Capital Issues
Expert Views on Today's Risk Capital and Human Capital Issues

Article 2 mins
Introduction: Clarity and Confidence to Make Better Decisions
Article 2 mins
The Age of Rising Resilience – An Economic Outlook
Article 3 mins
Building Resilience Against the Constant Cyber Threat
Article 2 mins
Making Better Decisions – A Treasurer’s Perspective
Article 2 mins
How to Balance the Conflicting Forces of Efficiency, Performance and Wellbeing
Article 3 mins
Seizing the Opportunity: Building a Comprehensive Approach to Risk Transfer
Article 2 mins
Tapping New Markets to Unlock Deal Value
Article 5 mins
The Rise of the Skills-Based Organisation
Article 2 mins
Creating a Fair and Equitable Workforce for Everyone
Article 3 mins
The Year of the Vote: How Geopolitical Volatility Will Impact Businesses
Article 2 mins
The Aon DifferenceThe construction industry is under pressure from interconnected risks and notable macroeconomic developments. Learn how your organization can benefit from construction insurance and risk management.

Article 8 mins
How North American Construction Contractors Can Mitigate Emerging Risks
Article 7 mins
Managing Construction Risks: 7 Risk Advisory Steps
Article 7 mins
Unlocking Capacity and Capital in a Challenging Construction Risk Market
Article 7 mins
Protecting North American Contractors from Extreme Heat Risks with Parametric
Article 5 mins
How Climate Modeling Can Mitigate Risks and Improve Resilience in the Construction Industry
Report 1 mins
Construction Risk Management Europe Report 2023
Article 8 mins
Parametric Can Help Mitigate Extreme Heat Risks for Contractors in EMEA
Article 9 mins
How the Construction Industry is Navigating Climate Change
Article 11 mins
Top Risks Facing Construction and Real Estate OrganizationsStay in the loop on today's most pressing cyber security matters.

Cyber Labs 17 mins
Maximizing value: How companies and pentesters can achieve more together
Cyber Labs 7 mins
DNSForge – Relaying with Force
Cyber Labs 14 mins
We’re All in This Together: The Case for Purple Teaming
Cyber Labs 7 mins
Parsing ESXi Logs for Incident Response with QELP
Cyber Labs 5 mins
Parsing Jenkins Configuration Files for Forensics and Fun
Cyber Labs 10 mins
Emerging Risks in Third-Party AI Solutions and How to Help Address Them
Cyber Labs 20 mins
Unveiling the Dark Side: Common Attacks and Vulnerabilities in Industrial Control Systems
Cyber Labs 9 mins
Mounted Guest EDR Bypass
Cyber Labs 6 mins
Optimizing Your Cyber Resilience Strategy Through CISO and CRO Connectivity
Cyber Labs 9 mins
Bypassing EDR through Retrosigned Drivers and System Time Manipulation
Cyber Labs 10 mins
DNSForge – Responding with Force
Cyber Labs 7 mins
Unveiling "sedexp": A Stealthy Linux Malware Exploiting udev Rules
Cyber Labs 3 mins
Command Injection and Path Traversal in StoneFly Storage Concentrator
Cyber Labs 7 mins
Adopt an AI Approach with Confidence, for CISOs and CIOs
Cyber Labs 3 mins
Responding to the CrowdStrike Outage: Implications for Cyber and Technology Professionals
Cyber Labs 10 mins
DUALITY Part II - Initial Access and Tradecraft Improvements
Cyber Labs 17 mins
Cracking Into Password Requirements
Cyber Labs 57 mins
DUALITY: Advanced Red Team Persistence through Self-Reinfecting DLL Backdoors for Unyielding Control
Cyber Labs 7 mins
Restricted Admin Mode – Circumventing MFA On RDP Logons
Cyber Labs 9 mins
Detecting “Effluence”, An Unauthenticated Confluence Web ShellOur Cyber Resilience collection gives you access to Aon’s latest insights on the evolving landscape of cyber threats and risk mitigation measures. Reach out to our experts to discuss how to make the right decisions to strengthen your organization’s cyber resilience.

Article 8 mins
Cyber and E&O Market Conditions Remain Favorable Amid Emerging Global Risks
Article 7 mins
How to Navigate AI-Driven Cyber Risks
Article 9 mins
Building Resilience in a Buyer-Friendly Cyber and E&O Market
Article 11 mins
A Middle Market Roadmap for Cyber Resilience
Article 7 mins
Lessons Learned from the CrowdStrike Outage: 5 Strategies to Build Cyber Resilience
Article 8 mins
Responding to Cyber Attacks: How Directors and Officers and Cyber Policies Differ
Article 7 mins
Why Now is the Right Time to Customize Cyber and E&O Contracts
Article 6 mins
8 Steps Toward Building Better Resilience Against Rising Ransomware Attacks
Article 7 mins
Mitigating Insider Threats: Managing Cyber Perils While Traveling Globally
Article 5 mins
Managing Cyber Risk through Return on Security Investment
Article 10 mins
Mitigating Insider Threats: Your Worst Cyber Threats Could be Coming from Inside
Article 9 mins
Why HR Leaders Must Help Drive Cyber Security Agenda
Article 10 mins
Escalating Cyber Security Risks Mean Businesses Need to Build ResilienceOur Employee Wellbeing collection gives you access to the latest insights from Aon's human capital team. You can also reach out to the team at any time for assistance with your employee wellbeing needs.

Article 8 mins
Employer Strategies for Cancer Prevention and Treatment
Article 6 mins
The Long-Term Care Conundrum in the United States
Article 9 mins
Developing a Paid Leave Strategy That Supports Workers and Their Families
Article 9 mins
4 Ways to Foster a Thriving Workforce Amid Rising Health Costs
Article 9 mins
The Next Evolution of Wellbeing is About Performance
Article 6 mins
Three Ways Collective Retirement Plans Support HR Priorities
Article 9 mins
How the Right Employee Wellbeing Strategy Impacts Microstress and Burnout at Work
Podcast 13 mins
On Aon Podcast: The Future of Healthcare: Key Factors Impacting Medical Trend Rates
Article 7 mins
Making Wellbeing Part of a Company’s DNA
Article 7 mins
A Comprehensive Approach to Financial WellbeingExplore Aon's latest environmental social and governance (ESG) insights.

Podcast 16 mins
On Aon Podcast: Approach to DE&I in the WorkplaceOur Global Insurance Market Insights highlight insurance market trends across pricing, capacity, underwriting, limits, deductibles and coverages.

Article 12 mins
Q4 2023: Global Insurance Market Overview
Article 13 mins
Top Risk Trends to Watch in 2024How do the top risks on business leaders’ minds differ by region and how can these risks be mitigated? Explore the regional results to learn more.

Article 12 mins
Top Risks Facing Organizations in Asia Pacific
Article 12 mins
Top Risks Facing Organizations in North America
Article 10 mins
Top Risks Facing Organizations in Europe
Article 8 mins
Top Risks Facing Organizations in Latin America
Article 8 mins
Top Risks Facing Organizations in the Middle East and Africa
Article 9 mins
Top Risks Facing Organizations in the United KingdomOur Human Capital Analytics collection gives you access to the latest insights from Aon's human capital team. Contact us to learn how Aon’s analytics capabilities helps organizations make better workforce decisions.

Article 35 mins
5 Human Resources Trends to Watch in 2025
Article 13 mins
Medical Rate Trends and Mitigation Strategies Across the Globe
Article 9 mins
3 Strategies to Help Avoid Workers Compensation Claims Litigation
Podcast 15 mins
On Aon Podcast: Using Data and Analytics to Improve Health Outcomes
Article 14 mins
How Technology Will Transform Employee Benefits in the Next Five Years
Podcast 18 mins
On Aon Podcast: Technology Impacting the Future of Health and Benefits
Article 8 mins
Integrating Workforce Data to Uncover Hidden Insights
Podcast 24 mins
On Aon’s Better Being Series: Measuring Wellbeing
Article 11 mins
Designing Tomorrow: Personalizing EVP, Benefits and Total RewardsExplore our hand-picked insights for human resources professionals.

Article 7 mins
COVID-19 has Permanently Changed the Way We Think About Wellbeing
Article 7 mins
DE&I in Benefits Plans: A Global Perspective
Article 10 mins
How Data and Analytics Can Optimize HR Programs
Article 9 mins
Why HR Leaders Must Help Drive Cyber Security Agenda
Article 7 mins
Case Study: The LPGA Unlocks Talent Potential with Data
Article 11 mins
Navigating the New EU Directive on Pay Transparency
Article 4 mins
How to Design Better Talent Assessment to Promote DE&I
Article 6 mins
Training and Transforming Managers for the Future of Work
Article 7 mins
Rethinking Your Total Rewards Programs During Mergers and Acquisitions
Article 14 mins
Building a Resilient Workforce That Steers Organizational Success | An Outlook Across IndustriesOur Workforce Collection provides access to the latest insights from Aon’s Human Capital team on topics ranging from health and benefits, retirement and talent practices. You can reach out to our team at any time to learn how we can help address emerging workforce challenges.

Article 35 mins
5 Human Resources Trends to Watch in 2025
Article 19 mins
3 Strategies to Promote an Inclusive Environment and Bridge the Gender Gap
Report 13 mins
A Workforce in Transition Prepares to Meet a Host of Challenges
Article 8 mins
2025 Salary Increase Planning Tips
Article 8 mins
Employer Strategies for Cancer Prevention and Treatment
Article 12 mins
Understanding and Preparing for the Rise in Pay Transparency
Podcast 12 mins
Better Being Series: Building Sustainable Performance in a Multi-Generational Workforce
Article 7 mins
Key Trends in U.S. Benefits for 2025 and Beyond
Article 8 mins
Pay Transparency Can Lead to Better Equity Across Benefits
Article 17 mins
3 Strategies to Improve Career Outcomes for Older Employees
Article 9 mins
Developing a Paid Leave Strategy That Supports Workers and Their Families
Article 9 mins
4 Ways to Foster a Thriving Workforce Amid Rising Health CostsOur Mergers and Acquisitions (M&A) collection gives you access to the latest insights from Aon's thought leaders to help dealmakers make better decisions. Explore our latest insights and reach out to the team at any time for assistance with transaction challenges and opportunities.

Article 8 mins
Exit Strategy Value Creation Opportunities Exist as Economic Pressures Persist
Article 5 mins
Future Trends for Financial Sponsors: Secondary Transactions
Article 7 mins
3 Ways to Unlock M&A Value in a Challenging Credit Environment
Article 7 mins
Rethinking Your Total Rewards Programs During Mergers and Acquisitions
Article 9 mins
Organizational Design and Talent Planning are Key to M&A Success
Article 7 mins
An Ever-Complex Global Tax Environment Requires Strong M&A Risk Solutions
Article 6 mins
Project Management for HR: The Secret Behind a Successful M&A Deal
Article 9 mins
Cultural Alignment Planning Drives M&A Success
Report 1 mins
A Guide to Maximizing Value in Post-Merger Integrations
Report 2 mins
The ABC's of Private Equity M&A: Deal Flow Impacts of Al, Big Tech and Climate Change
Article 11 mins
The Silver Lining on M&A Deal Clouds: M&A Insurance Insights from 2023How do businesses navigate their way through new forms of volatility and make decisions that protect and grow their organizations?
Our Parametric Insurance Collection provides ways your organization can benefit from this simple, straightforward and fast-paying risk transfer solution. Reach out to learn how we can help you make better decisions to manage your catastrophe exposures and near-term volatility.

Article 10 mins
How Public Entities and Businesses Can Use Parametric for Emergency Funding
Article 6 mins
Parametric Insurance: A Complement to Traditional Property Coverage
Article 8 mins
Using Parametric Insurance to Match Capital to Climate Risk
Article 6 mins
Using Parametric Insurance to Close the Earthquake Protection Gap
Article 5 mins
How Technology Enhancements are Boosting ParametricOur Pay Transparency and Equity collection gives you access to the latest insights from Aon's human capital team on topics ranging from pay equity to diversity, equity and inclusion. Contact us to learn how we can help your organization address these issues.

Article 19 mins
3 Strategies to Promote an Inclusive Environment and Bridge the Gender Gap
Report 1 mins
The 2024 North America Pay Transparency Readiness Study
Article 10 mins
How Financial Institutions can Prepare for Pay Transparency Legislation
Article 8 mins
Pay Transparency Can Lead to Better Equity Across Benefits
Article 12 mins
Understanding and Preparing for the Rise in Pay Transparency
Podcast 14 mins
On Aon Podcast: Understanding Pay Transparency Regulations
Article 11 mins
Navigating the New EU Directive on Pay Transparency
Article 7 mins
To Disclose Pay or Not? How Companies are Approaching the Pay Transparency Movement
Podcast 19 mins
On Aon Podcast: Better Being Series Dives into Women’s Health
Article 11 mins
Advancing Women’s Health and Equity Through Benefits and SupportForecasters are predicting an extremely active 2024 Atlantic hurricane season. Take measures to build resilience to mitigate risk for hurricane-prone properties.

Article 8 mins
Florida Hurricanes Not Expected to Adversely Affect Property Market
Article 10 mins
Build Resilience for an Extremely Active Atlantic Hurricane Season
Article 6 mins
Four Steps to Develop Strong Property Risk Coverage in a Hardening Market
Podcast 16 mins
On Aon Podcast: Navigating and Preparing for Catastrophes
Article 6 mins
Parametric Insurance: A Complement to Traditional Property Coverage
Article 6 mins
Navigating Climate Risk Using Multiple Models and Data Sets
Article 5 mins
Rising Losses From Severe Convection Storms Mostly Explained by Exposure Growth
Article 6 mins
Using Parametric Insurance to Close the Earthquake Protection GapOur Technology Collection provides access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities of technology. Reach out to the team to learn how we can help you use technology to make better decisions for the future.

Article 23 mins
The AI Data Center Boom: Strategies for Sustainable Growth and Risk Management
Article 7 mins
How Technology is Transforming Open Enrollment in the U.S.
Article 15 mins
Navigating Cyber Risks in EMEA: Key Insights for 2025
Article 7 mins
How to Navigate AI-Driven Cyber Risks
Article 16 mins
How Artificial Intelligence is Transforming Human Resources and the Workforce
Report 18 mins
Evolving Technologies Are Driving Firms to Harness Opportunities and Defend Against Threats
Alert 3 mins
Better Decisions Brief: Perspectives on the CrowdStrike Outage
Podcast 9 mins
On Aon Podcast: How has CrowdStrike Changed the Cyber Market?
Article 12 mins
5 Ways Artificial Intelligence can Boost Claims Management
Article 12 mins
Navigating AI-Related Risks: A Guide for Directors and Officers
Article 5 mins
How Technology Enhancements are Boosting Parametric
Article 9 mins
How to Futureproof Data and Analytics Capabilities for ReinsurersTrade, technology, weather and workforce stability are the central forces in today’s risk landscape.

Article 7 mins
Cyber Attack or Data Breach
Article 4 mins
Business Interruption
Article 4 mins
Economic Slowdown or Slow Recovery
Article 5 mins
Failure to Attract or Retain Top Talent
Article 5 mins
Regulatory or Legislative Changes
Article 4 mins
Supply Chain or Distribution Failure
Article 6 mins
Commodity Price Risk or Scarcity of Materials
Article 4 mins
Damage to Brand or Reputation
Article 5 mins
Failure to Innovate or Meet Customer Needs
Article 4 mins
Increasing Competition
Report 3 mins
Business Decision Maker SurveyOur Trade Collection gives you access to the latest insights from Aon's thought leaders on navigating the evolving risks and opportunities for international business. Reach out to our team to understand how to make better decisions around macro trends and why they matter to businesses.

Podcast 9 mins
Special Edition: Global Trade and its Impact on Supply Chain
Article 8 mins
The Evolving Threat of Cargo Theft: 5 Key Mitigation Strategies
Report 3 mins
Global Risk Management Survey
Report 13 mins
Wide-Ranging Trade Issues Confront Global Businesses on Multiple Fronts
Article 6 mins
Four Steps to Develop Strong Property Risk Coverage in a Hardening Market
Article 14 mins
Cutting Supply Chains: How to Achieve More Reward with Less Risk
Article 9 mins
Driving Private Equity Value Creation Through Credit Solutions
Article 7 mins
4 Steps to Help Take Advantage of a Buyer-Friendly Directors' & Officers' Market
Article 9 mins
Managing Reputational Risks in Global Supply Chains
Article 6 mins
How an Outsourced Chief Investment Officer Can Help Improve Governance and Manage Complexity
Article 8 mins
Decarbonizing Your Business: Finding the Right Insurance and Strategy
Article 8 mins
Reputation Analytics as a Leading Indicator of ESG RiskWith a changing climate, organizations in all sectors will need to protect their people and physical assets, reduce their carbon footprint, and invest in new solutions to thrive. Our Weather Collection provides you with critical insights to be prepared.

Podcast 9 mins
On Aon Podcast: Climate Impact on the Property and Casualty Market
Alert 14 mins
L.A. Wildfires Highlight Urgent Need for Employee Support and Business Resilience
Report 18 mins
Climate Analytics Unlock Capital to Protect People and Property
Report 2 mins
Climate and Catastrophe Insight
Article 10 mins
How Public Entities and Businesses Can Use Parametric for Emergency Funding
Podcast 12 mins
On Aon Podcast: Tackling Climate Risk to Build Economic Resilience
Article 8 mins
Understanding Freeze Risk in a Changing Climate
Podcast 9 mins
On Aon Podcast: Climate Science Through Academic Collaboration
Article 6 mins
How Companies Are Using Climate Modeling to Improve Risk Decisions
Article 8 mins
Using Parametric Insurance to Match Capital to Climate Risk
Article 9 mins
How the Construction Industry is Navigating Climate Change
Article 9 mins
Record Heatwaves: Protecting Employee Health and SafetyOur Workforce Resilience collection gives you access to the latest insights from Aon's Human Capital team. You can reach out to the team at any time for questions about how we can assess gaps and help build a more resilience workforce.

Article 4 mins
Using Data to Close Workforce Gaps in Financial Institutions
Article 5 mins
Using Data to Close Workforce Gaps in Retail Companies
Article 7 mins
Using Data to Close Workforce Gaps in Technology Companies
Article 5 mins
Using Data to Close Workforce Gaps in Manufacturing Companies
Article 6 mins
Using Data to Close Workforce Gaps in Life Sciences Companies
Report 4 mins
Measure Workforce Resilience for Better Business Outcomes
Podcast 18 mins
On Aon Podcast: Methodology to Predict Employee Performance for the LPGA
Article 6 mins
Training and Transforming Managers for the Future of Work
Article 14 mins
Building a Resilient Workforce That Steers Organizational Success | An Outlook Across IndustriesYou will soon receive an email to verify your email address. Please click on the link included in this note to complete the subscription process, which also includes providing consent in applicable locations and an opportunity to manage your email preferences.

Article 5 Min Read

Article 10 Min Read
Your request is being reviewed so we can align you to the best resources on our team. In the meantime, we invite you to explore some of our latest insights below.

Article 5 Min Read

Article 10 Min Read
If you encounter an issue, use the link below to start a new download.
Download Now